

30 October 2019
Office 365 Learnings
During the first half of 2019 we have seen the number of Office 365 (O365) environment compromises rise, and assisted several customers with O365 incident response services.
The key learnings we can take from these engagements, and our market observations demonstrate that:
- Even well managed and mature sites have been compromised.
- It is important to know all your data aggregation points at all times.
- Data sharing across the O365 environment is misunderstood.
- Identifying termination points, where data can be readily shared with external parties, is critical.
- Cloud service mapping and effective management reduces unnecessary risks and exposures.
- Knowledge of all O365 capabilities and security dashboards aids prevention or early detection.
In a nutshell, being proactive with regular security configuration checks, data exposure checks, logging and dashboard fine-tuning helps to keep users safe and incidents at bay.
To view the details on our Office 365 Security Audit service Click Here
Context is King
A recent assignment we undertook for an unnamed organisation (we’ll call them Demonstration City Council (DCC) for the purposes of this article) required us to review and conduct a gap analysis of their existing IT policy material.
In doing the analysis the most obvious gaps we identified were that DCC did not have any IT policies written for heads of department, team leaders or managers, and there were only limited policies in place for the technical team. The scope and context of their existing policies were focused on acceptable use only, therefore, people in the organisation that were required to make decisions to approve and enable access to council systems and data had no guidelines as to what the council expected of them.
After consideration the leadership team at DCC decided this issue presented a risk they needed to address and that they should work with us to mitigate it.
With the understanding that developing, delivering and managing policies in general can be a challenge, it is very important to have policies in place with the right scope and context.
The table below contains examples of the key policy statement headings that one should consider for use in a comprehensive Access Control Policy scope for:
- A general user (U) - General User Policy Content
- A manager/team leader (M) - Management Policy Content
- A technical team member (T) - Technical Policy Content
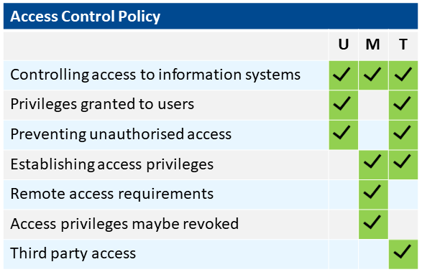
Click Here to view a comparison chart of the sample policy content applicable to a user, a manager, and a technical person. The chart details policy statements applicable to controlling access to information systems, which is one of a number of key elements that make up a good Access Control Policy.
In a typical IT Policy System project we assist customers to develop and deliver a suite of up to 26 effective policies written in user friendly plain English. Usually up to 10 of these policies are written contextually for users, managers and technical people covering topics such as Access Control, Computer Systems and Use, Information Management and Personnel Management.
Watch a 5 minute demo video of the IT Policy System
Cyber Insurance
A recent article we spotted suggested that the global cyber insurance market was set to grow to US$22.8 billion by 2024. The market was estimated to be worth US$3.5-4.2 billion in 2017.
This projected growth in the market should help it to mature and improve the understanding of both customers and insurers about evolving cyber risks, data-driven cyber policies, and how to underwrite them.
On a local level there is still some valid caution being applied by small and medium businesses as to the benefits of insuring. Where applicable new or increased regulatory compliance is a likely catalyst for organisations to put cyber insurance cover in place, as has been seen in parts of the US and Europe.
Cyber insurance policies cannot prevent breaches. They are meant to provide you with the financial support to address a cyber incident quickly, so that you can minimise and manage any potential financial and reputational damage. The policies generally do not cover the financial impact of losses of intellectual property, reputational damage, or theft of your trade secrets.
An organisation is still going to be required to make the right level of investment in security fundamentals (policies, procedures, education and awareness, controls etc.) and you should expect any credible insurer will want to validate your security posture when putting forward policy options.
To discuss how Kaon Security can assist your organisation create and maintain a secure IT environment contact Mike Conboy.
