


10 April 2018
Vulnerability testing, cloud migrations, Policy Lite and PolicyConnect released
We are pleased to advise Kaon Security have started shipping the Policy Lite System as of 29th March to the local market.
This Cloud delivered solution is designed to assist organisations with under 200 users lay the foundations for a secure computing environment. The suite of policies is customised and branded for each organisation and provides users with easy to read policy content outlining what is acceptable use of company systems and data.
Having assisted many large and medium organisations get the foundations right for creating a secure computing environment, Kaon Security worked with the developers, Protocol Policy Systems, to build this new version. The Policy Lite version provides a suite of Acceptable Use focussed policies that are mapped to the ISO27002 standard plus a selection of associated forms, logs and guidelines. Once deployed all updating of the policy content regarding policy wording edits, terminology and standards are taken care of by Kaon Security for each customer.
Available on an annual subscription basis the Policy Lite implementation process is designed to be completed within 28 days (elapsed timeframe) and entails a Security Consultant running a 4 hour online workshop with the stakeholders at each customer site. To view more detail CLICK HERE.
Spreading the word - PolicyConnect
PolicyConnect has been designed to help organisations proactively “socialise” the contents of their IT Policy System. Having worked with a customer on this project in the last 2 months we are pleased to be able to announce PolicyConnect is immediately available as an add-on to the IT Policy System.
PolicyConnect will allow your organisation to deliver policy content to Users, in an always on-top pop-up window, when organisational users login.
Once a user has reviewed the information on screen, they can then opt to click either the “I Acknowledge” button or the “Close Without Acknowledge” button, closing the always on-top window.
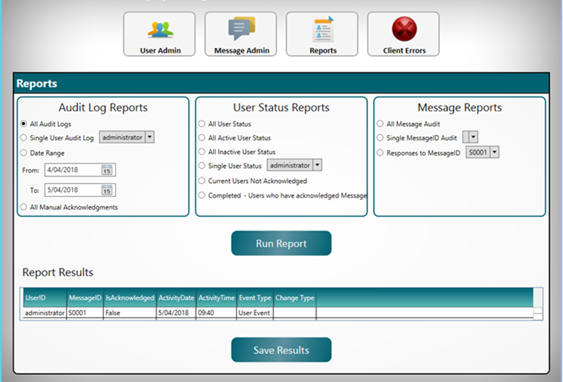
The actions of the User are recorded in an administration database. As a PolicyConnect administrator you can monitor trends, for example, which team members are choosing to select the “I Acknowledge” or “Close Without Acknowledge” option (see User and Administration screenshots below)
At anytime an Administrator can export PolicyConnect reports (csv format) and use them to report on compliance and where appropriate follow up on any issues or queries regarding the policy content.
For a demonstration or discussion regarding Policy Lite and/or PolicyConnect contact Mike Conboy or Steve Macmillan.

5 key points to consider about a Vulnerability Assessment
1. How do we know our nominated provider is testing correctly? - our weakest point defines the overall security posture.
2. What type of Vulnerability Assessment is required? - infrastructure, web application, mobile, wireless, cloud. There are many types of vulnerability assessments.
3. Which methodology should be followed to complete an assessment and attain the right testing outcomes? – e.g OWASP for web application testing, PCIDSS compliant assessment etc.
4. How can we maximise the value of our assessment outcome? – create an action list for patch management, compile a developer report for defect fixing etc.
5. Do we need a Black-box, Grey-box or White-box approach? – how do we define the outcome from a specific attacker - external or internal perspective.
If you are intending to conduct a Vulnerability Assessment it maybe worth booking an hour with one of our consultants to undertake some initial planning before going to market. For more information contact Mike Conboy.
5 key points to consider about Cloud Migration and Security
1. Know your data - This includes the data location, format, category, classification, security, transferability and segregation aspects.
2. What are the considerations for the 3 critical components of security - Confidentiality, Integrity, and Availability (CIA)?
3. Are provisions in place for logging, auditing and monitoring aspects during and after the cloud migration?
4. Could there be any business continuity and legal implications if your data storage is “cross border” and infrastructure becomes unavailable?
5. Have you considered exploiting this opportunity to achieve compliance, improved security posture and cost benefits?
Migrating to the Cloud represents a great opportunity for most organisations, from a number of business and operational facets. However the process is fraught with risk unless thorough advance planning and preparation is conducted with regards to security. To discuss how we have assisted clients ensure they have a positive outcome from a migration exercise contact Steve Macmillan.
