


15 March 2019
Which Essential controls should be at the top of your list?
Plenty of good guidance is available to help improve an organisation’s information security. In Australia and New Zealand organisations such as the Australian Signals Directorate (ASD) and Cert NZ publish very useful lists, to help us prioritise which controls to implement, based on the threat and incident data that is available to them.
The Essential 8 (ASD) and Top 10 (Cert NZ) are seen as a good baseline from which to defend against a compromise of IT systems. The table below combines these critical controls; we can see that 5 of them are recommended by both ASD and Cert NZ, with the balance of 7 being a unique recommendation from either body.
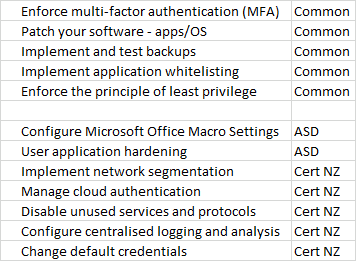
Many of these controls are still not being implemented by organisations in ANZ and as a result they are more likely to suffer some form of IT security incident. Our consultants can assist an organisation to develop an improvement plan that will assess what systems and data need to be protected, determine what level of protection should initially be applied and thereafter help drive an implementation exercise.
Click here to view the Essential 8 and Top 10 details.
Over the next 4 weeks a policy mapping exercise will be completed and available in the IT Policy System for these controls. Click Here to view a brief video clip.
Worth the effort
Business email compromise (BEC) continues to be a costly issue. Cybercriminals continue to use a combination of online research and social engineering, to net a healthy payday from a wide range of organisational types in finance, manufacturing and other business sectors
It is well worth the effort to set up some training and awareness sessions on this topic for members of your organisation, particularly those that work in finance and management.
How does BEC work?
Executives targeted
Cybercriminals start their BEC scamming campaign by conducting research on target individuals, typically those who occupy high level positions in an organisation. The sources of information used include LinkedIn profiles, company website profiles and information that a search engine can provide such as news articles.
A spear phishing attack on the target individual(s) is then applied to get access to corporate systems. When they are on the “inside” the cybercriminals have the ability to build a picture of how financial transactions are handled by this individual and the target company.
Most commonly the cybercriminal sends an email from the account of the individual that has been profiled to request for a transfer of funds. The email will state there is some urgency and a specific timeframe to get funds transferred to an account under the control of the cybercriminal or an associate.
Variations of the BEC scam - invoice fraud and legal impersonation
For the invoice fraud scam the cybercriminal gains access to a trusted supplier’s email account through a targeted attack. They can then view real examples of the supplier’s invoices and start to deliver fake invoices to business customers. Modified invoices will include new bank account information, and if an accounts payable person does not question this, it is highly probable that the fake invoice will be processed for payment.
In the legal impersonation example a cybercriminal pretends to be a lawyer or representative from a legal firm requesting payment for an urgent and confidential matter.
Security awareness training on business email compromise (BEC) is highly recommended and ideally it should incorporate an advanced phishing simulation programme. Over time an advanced phishing programme should improve a user’s ability to identify fake emails, fake email domains and malicious links used by a cybercriminal.
Some other steps to consider are: -
- Employees should be encouraged to be suspicious and alert regarding any urgent or confidential requests to conduct a financial transaction.
- Caution should apply to changes in business practices or customer and supplier payment details e.g. a supplier invoice has a changed (different) account number.
- If possible, request that the posting of personal information to social media that might include work related information (e.g. overseas travel) is avoided as this is potentially useful information in the wrong hands.
To discuss how the Essential 8 or Top 10 can give your organisation a good baseline of defence or to understand how to build better security awareness within your team, contact us.
